
Dataflow Analysis
Explorer the Dataflow Analyzer which forms the core capability of wSAST.
Learn moreFlexible static code analysis framework for security consultants.
wSAST is a cutting-edge static analysis framework designed to help optimize your code review process. The framework aims to empower security consultants by providing a comprehensive suite of utilities tailored to enhance the ease with which code reviews are performed.
The framework is designed specifically to be used by security consultants that operate under heavy time constraints, with missing code and dependencies, or with code which cannot be compiled. wSAST aims to free up valuable consultant time by automating routine analysis and assisting with code comprehension.
wSAST is designed to be able to support multiple languages within the same project, allowing minimalistic bridging code to be written where necessary to facilitate cross-language analysis.
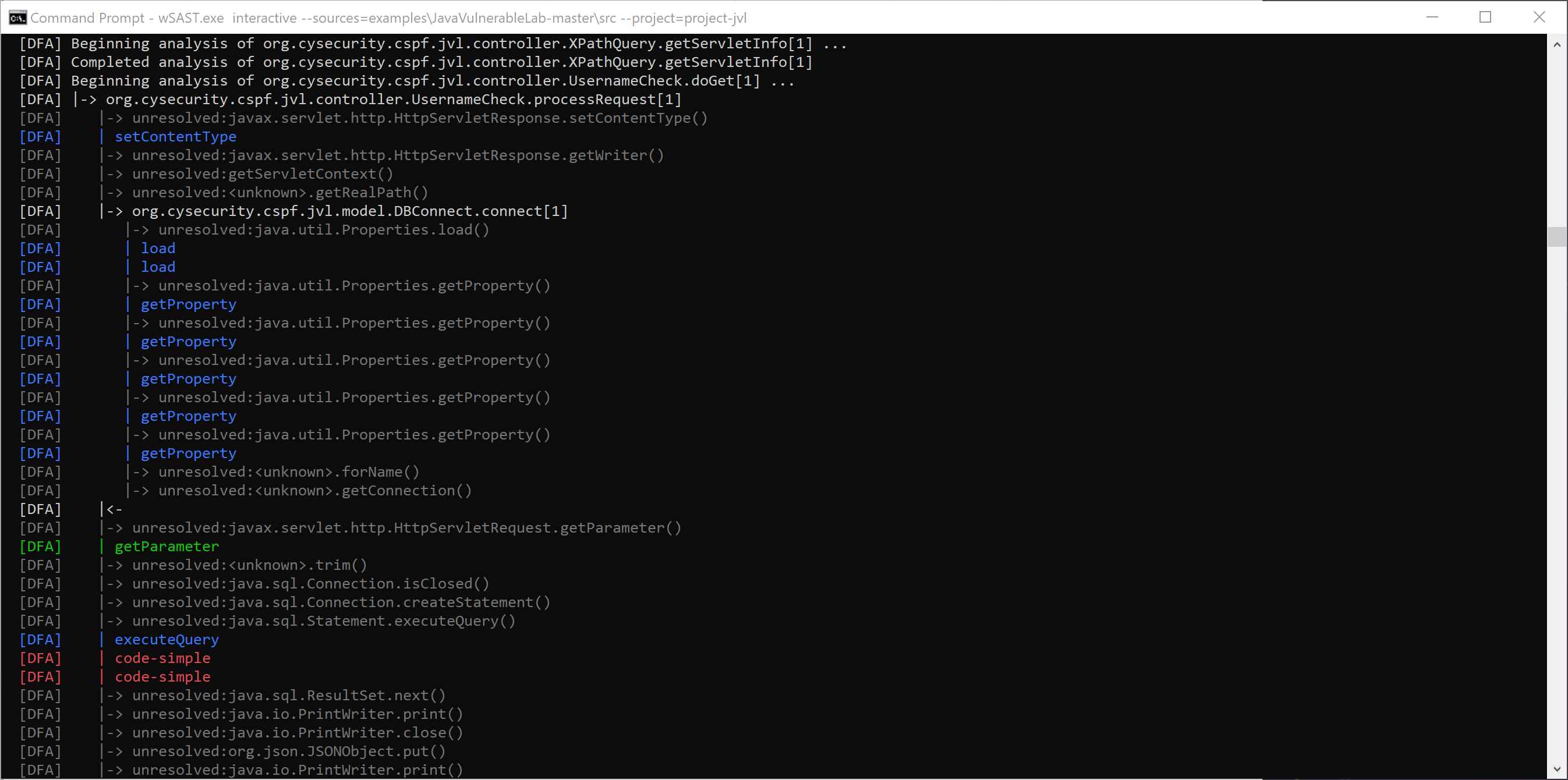
wSAST implements a full dataflow analyzer capable of performing source-to-sink analysis. Sources can be completely user defined, either using our Common Rules Engine XML format, or implemented manually as .NET plugins. Sources and sinks can be defined using any part of the application syntax tree (e.g. any node type) and/or application state as accessible at runtime via the dataflow engine. Multiple sinks can be linked together for more complicated findings, and arbitary links between tainted variables can be established and persisted throughout analysis. User data can be attached to any dataflow variable for especially intricate results.
wSAST also provides static AST-only derived rules which can be used to identify bad coding patterns or vulnerabilities in place without the need to perform dataflow analysis. This enables a wide variety of findings to be made before dataflow analysis completes. Rules can be defined either using our Common Rules Engine XML format, or implemented manually as .NET plugins.
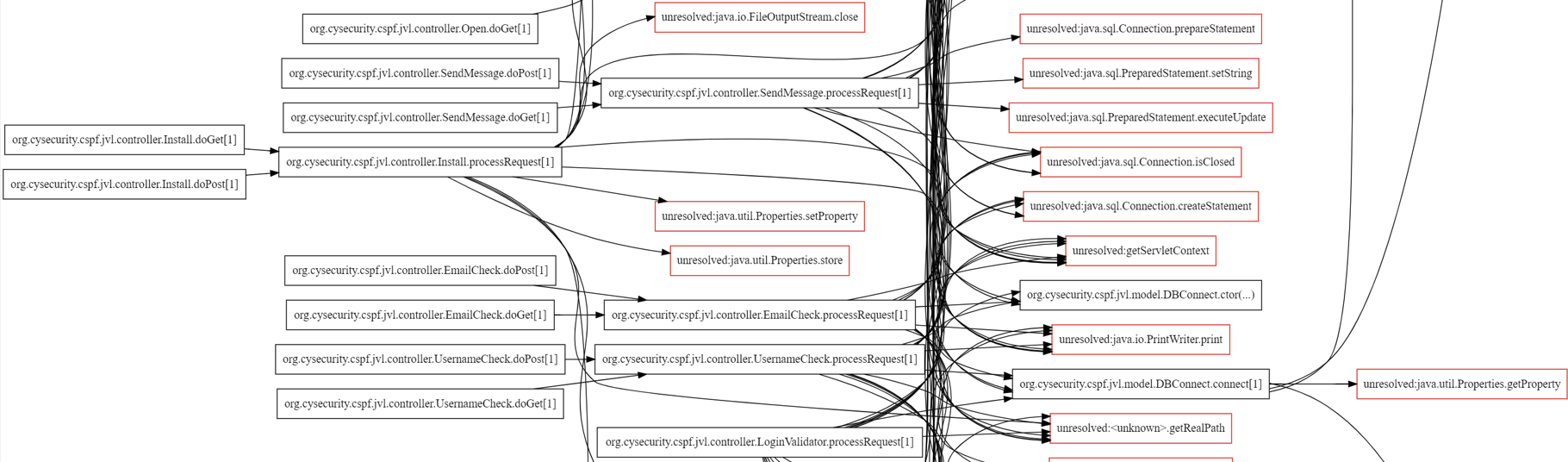
wSAST provides the ability to generate graphviz output for class relationships, call flow, syntax tree and local control flow. These graphs can be generated across the entire codebase, or constrained using regex to focus on only the classes, areas and potential class/method names of interest. Entrypoints and specific flows matching user-defined regex can be highlighted for easier analysis.
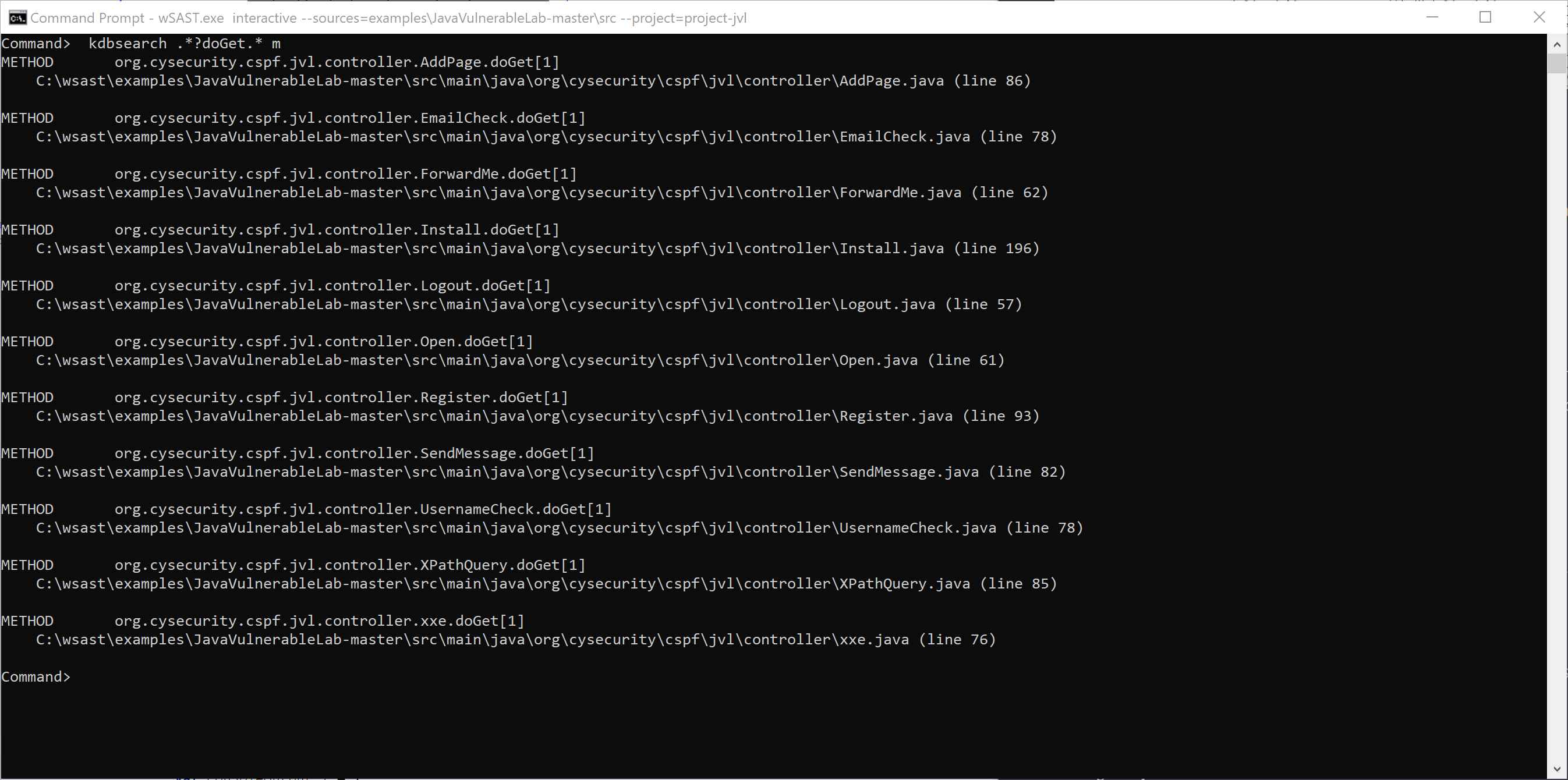
wSAST enables searching of the processed code using a text-based REPL approach, using regex to specify names of namespaces, classes, methods and variables of interest. Searches can be constrained using negative regex matching to exclude code of interest, and type constraints can also be applied. If required the raw AST can also be searched against, in addition to the processed codebase.
wSAST provides the ability to graph calls to and from methods matching specific names using regex (e.g. any method in a class with ".*?auth.*" in the name, or any calls to "mem(cpy|move)"). The depth of the call stacks to and from the specified methods can be constrained.
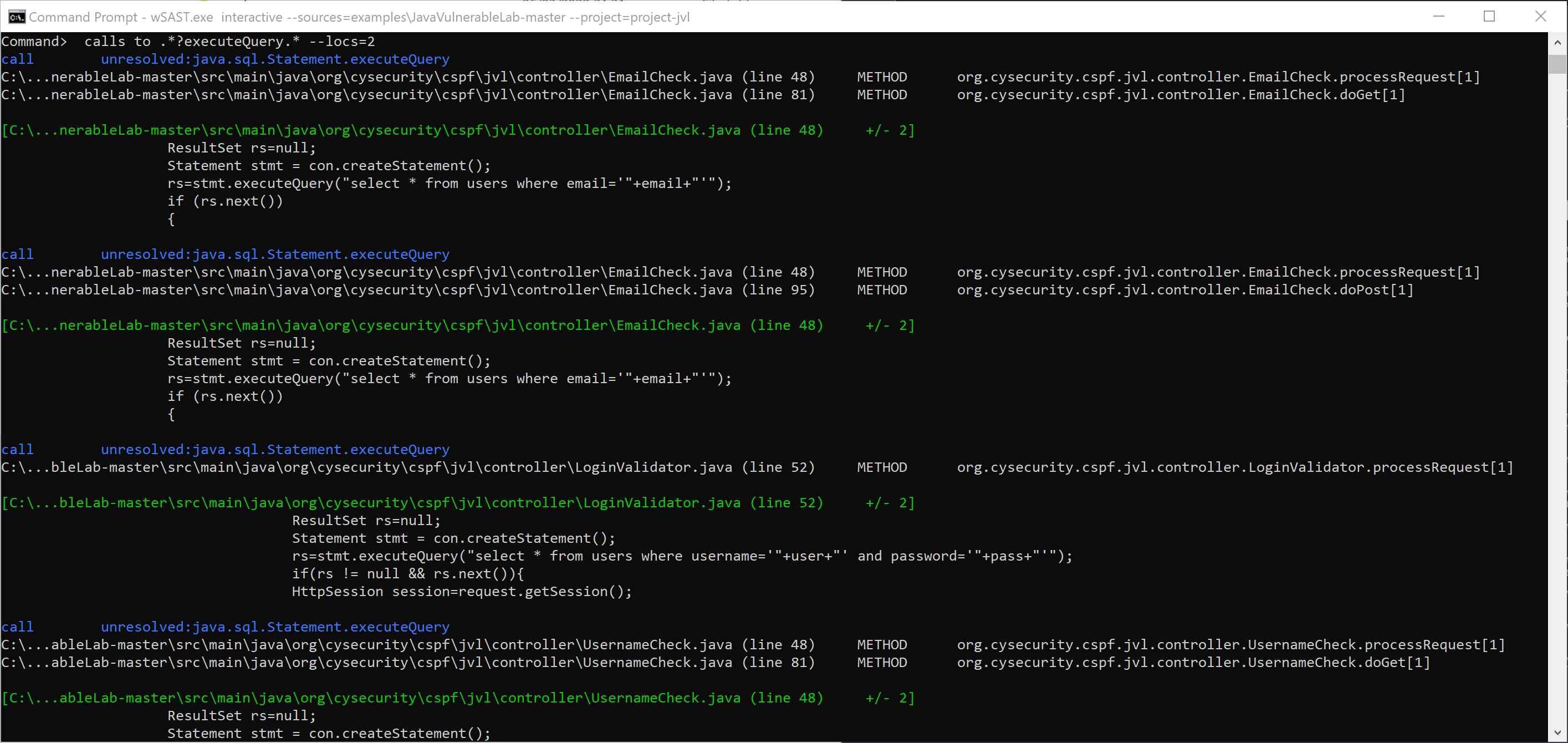
wSAST facilitates the discovery of paths between methods matching specific names (e.g. show me all calls between "http\.request.*" and ".*?database.*") and can print all matching flows.
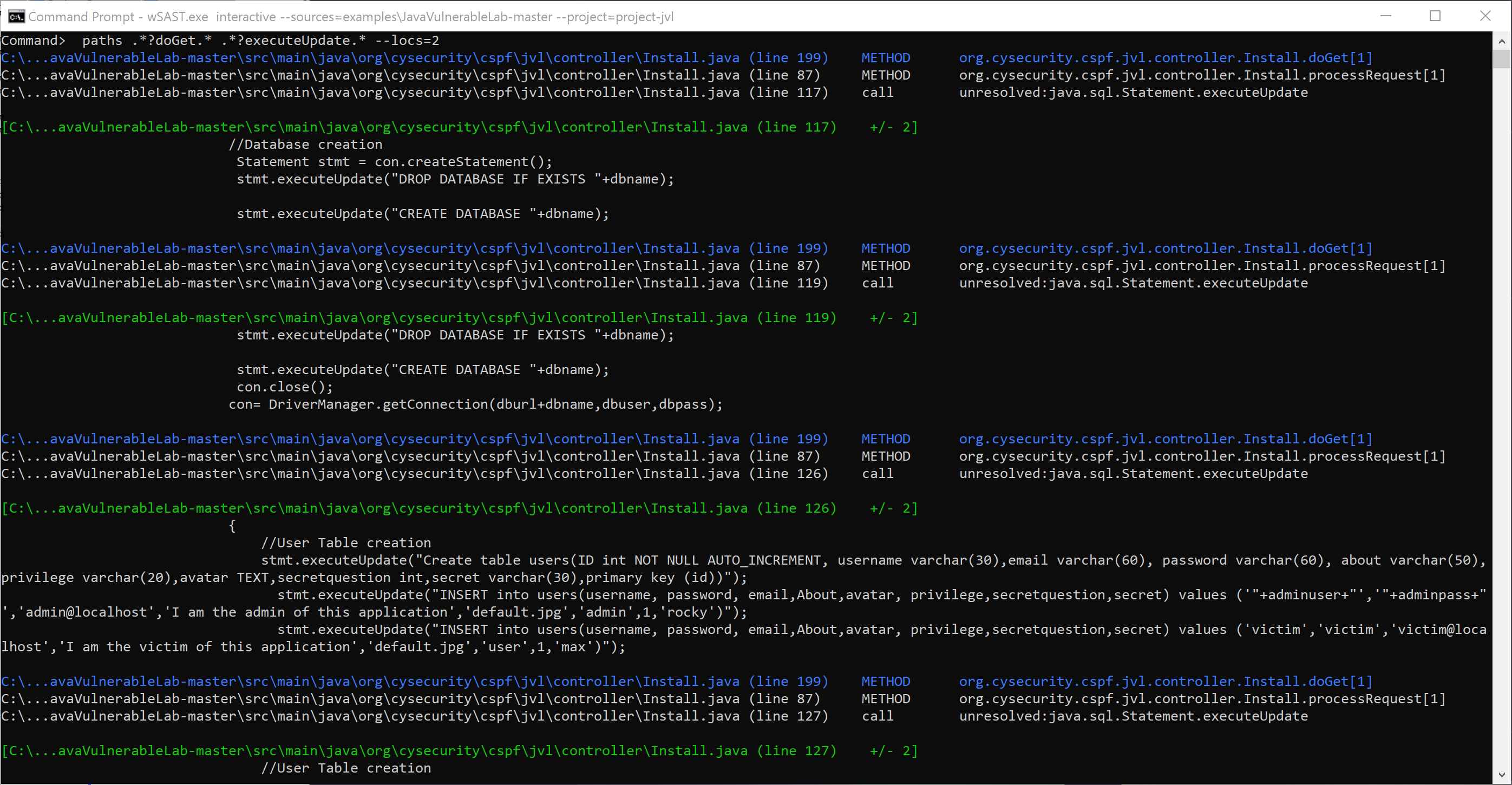
wSAST is designed to work with incomplete code and code with missing dependencies; it does not require any compilation and can analyse codebases in any state of development.
During analysis the maximum amount of definite information that can be extracted from the code is stored, and then during dataflow analysis missing code is inferred by building up information on missing types as execution proceeds. Taint controls can also enable improved handling of missing code (e.g. by specifying that tainting a data member of a class for which the code is missing taints the entire instance).
For cases where missing code cannot be reasonably inferred it is easy to use the wSAST Intermediary Language (WSIL) - a Java-like language - to represent the missing code in a superficial way to augment analysis and enable missing framework behaviours to be understood. For many frameworks these shims can be write-once-use-everywhere, reducing future effort.
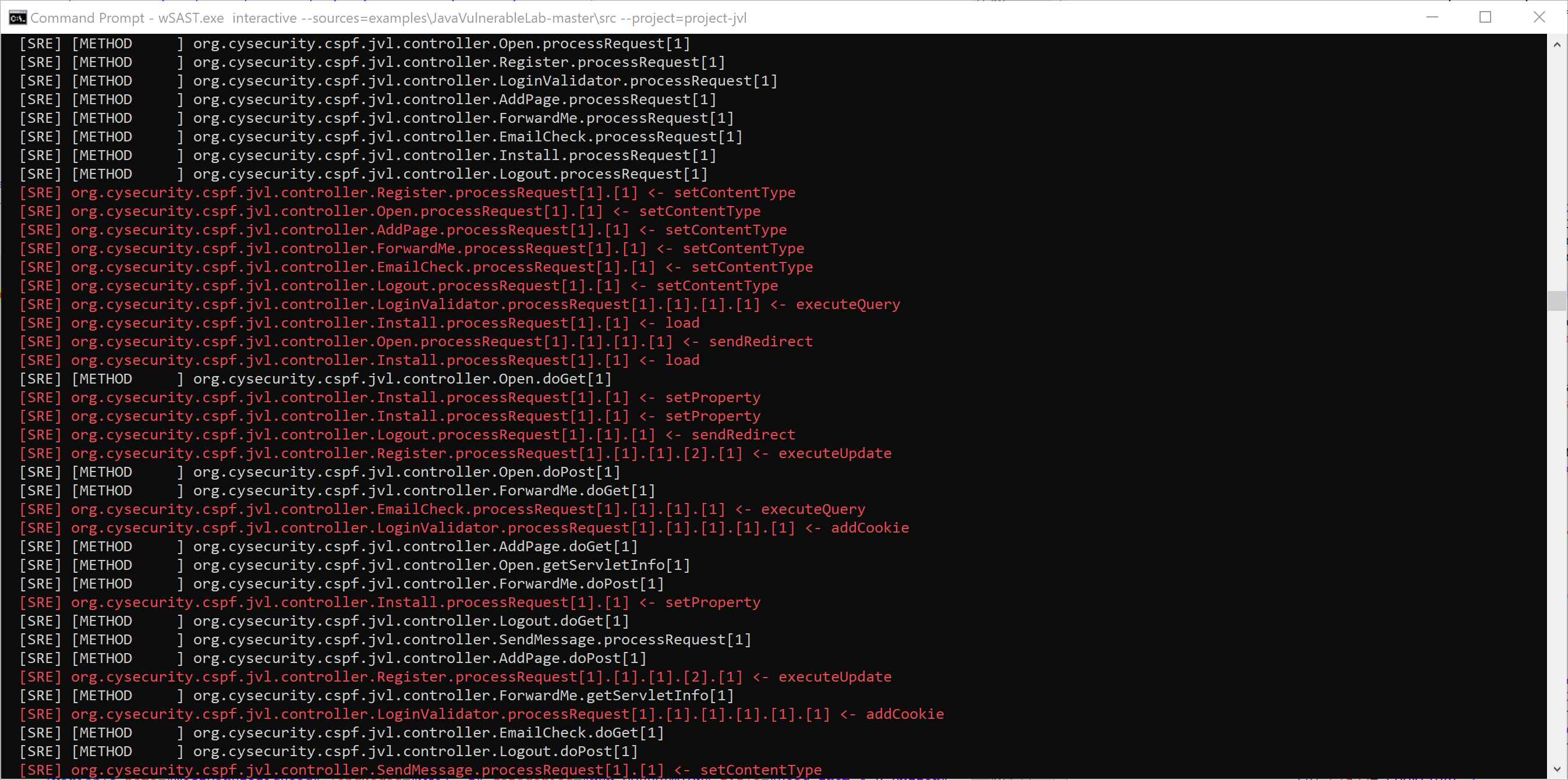
Reporting is performed through a plugin model where each format implements a straightforward interface which is invoked whenever a new finding is made by the Dataflow Engine or Static Analyzer. The default reporting plugin code-simple reports each finding as a simple code flow summary, line-by-line, with a description of the issue. New plugins can be developed easily to report to any format required, including graphical output to illustrate exact paths through the codebase.

Explorer the Dataflow Analyzer which forms the core capability of wSAST.
Learn more
Learn more about the Static Analysis capabilities.
Learn more
Discover the powerful code graphing capabilities which can aid you in code exploration.
Learn more
See how code searching can help you quickly determine possible paths to exploitation.
Learn more