
Dataflow Analysis
Explorer the Dataflow Analyzer which forms the core capability of wSAST.
Learn moreFlexible static code analysis framework for consultants and developers.
The wSAST framework also provides the ability to search the codebase under analysis. Searching can be performed against the processed source code (via the knowledge base) or directly against the ASTs. Searching not only allows identification of specific types and functions etc. within the code but also allows for listing of calls to and from these, and the listing of paths between functions.
kdbsearch Search knowledge base entries
kdbsearch [...]
- comma separated regex of KDB entries (multiple means OR, ! prefix means AND NOT)
[types] - [g]lobal, [n]amespace, [i]nterface, [cl]ass, [m]ethod, [co]nstructor, [b]lock, [v]ariable
astsearch Search AST
astsearch [...]
- comma separated regex (multiple means OR, ! prefix means AND NOT)
[types] - [t]ype, [l]abel, [v]alue
[--filter=] - comma separated regex of KDB entries (multiple means OR, ! prefix means AND NOT)
calls List calls to and from specific methods
calls [...]
- to, from
- comma separated regex of KDB method entries (multiple means OR, ! prefix means AND NOT)
[depth] - depth of calls to trace (default: 99999)
paths Find paths connecting functions
paths [depth]
- comma separated regex of KDB entries (multiple means OR, ! prefix means AND NOT)
- comma separated regex of KDB entries (multiple means OR, ! prefix means AND NOT)
[depth] - depth of calls to trace (default: 99999)
The knowledge base (kdb) contains information on all analyzed code after translation to WSIL. After analysis the entire knowledge base is written to a project file (knowledgedb.txt) along with all known entrypoints (entrypoints.txt).
The knowledge base can be searched by regular expressions using the famililar syntax allowing for both inclusive and exclusive matching. In addition to regex it is possible to filter by the code object type being searched (for example, classes, methods, variables).
An example of searching for all methods matching doPost, all classes matching Register and all variables matching Pass or pass follows:
Command> kdbsearch .*?doPost.* m
METHOD org.cysecurity.cspf.jvl.controller.AddPage.doPost[1]
C:\wsast\examples\JavaVulnerableLab-master\src\main\java\org\cysecurity\cspf\jvl\controller\AddPage.java (line 100)
METHOD org.cysecurity.cspf.jvl.controller.EmailCheck.doPost[1]
C:\wsast\examples\JavaVulnerableLab-master\src\main\java\org\cysecurity\cspf\jvl\controller\EmailCheck.java (line 93)
METHOD org.cysecurity.cspf.jvl.controller.ForwardMe.doPost[1]
C:\wsast\examples\JavaVulnerableLab-master\src\main\java\org\cysecurity\cspf\jvl\controller\ForwardMe.java (line 76)
METHOD org.cysecurity.cspf.jvl.controller.Install.doPost[1]
C:\wsast\examples\JavaVulnerableLab-master\src\main\java\org\cysecurity\cspf\jvl\controller\Install.java (line 210)
METHOD org.cysecurity.cspf.jvl.controller.Logout.doPost[1]
C:\wsast\examples\JavaVulnerableLab-master\src\main\java\org\cysecurity\cspf\jvl\controller\Logout.java (line 71)
METHOD org.cysecurity.cspf.jvl.controller.Open.doPost[1]
C:\wsast\examples\JavaVulnerableLab-master\src\main\java\org\cysecurity\cspf\jvl\controller\Open.java (line 75)
METHOD org.cysecurity.cspf.jvl.controller.Register.doPost[1]
C:\wsast\examples\JavaVulnerableLab-master\src\main\java\org\cysecurity\cspf\jvl\controller\Register.java (line 107)
METHOD org.cysecurity.cspf.jvl.controller.SendMessage.doPost[1]
C:\wsast\examples\JavaVulnerableLab-master\src\main\java\org\cysecurity\cspf\jvl\controller\SendMessage.java (line 96)
METHOD org.cysecurity.cspf.jvl.controller.UsernameCheck.doPost[1]
C:\wsast\examples\JavaVulnerableLab-master\src\main\java\org\cysecurity\cspf\jvl\controller\UsernameCheck.java (line 92)
METHOD org.cysecurity.cspf.jvl.controller.XPathQuery.doPost[1]
C:\wsast\examples\JavaVulnerableLab-master\src\main\java\org\cysecurity\cspf\jvl\controller\XPathQuery.java (line 99)
METHOD org.cysecurity.cspf.jvl.controller.xxe.doPost[1]
C:\wsast\examples\JavaVulnerableLab-master\src\main\java\org\cysecurity\cspf\jvl\controller\xxe.java (line 90)
Command> kdbsearch .*?Register.* cl
CLASS org.cysecurity.cspf.jvl.controller.Register
C:\wsast\examples\JavaVulnerableLab-master\src\main\java\org\cysecurity\cspf\jvl\controller\Register.java (line 26)
Command> kdbsearch .*?[Pp]ass.* v
VARIABLE org.cysecurity.cspf.jvl.controller.Install.dbpass
C:\wsast\examples\JavaVulnerableLab-master\src\main\java\org\cysecurity\cspf\jvl\controller\Install.java (line 33)
VARIABLE org.cysecurity.cspf.jvl.controller.Install.adminpass
C:\wsast\examples\JavaVulnerableLab-master\src\main\java\org\cysecurity\cspf\jvl\controller\Install.java (line 37)
VARIABLE org.cysecurity.cspf.jvl.controller.LoginValidator.processRequest[1].[1].pass
C:\wsast\examples\JavaVulnerableLab-master\src\main\java\org\cysecurity\cspf\jvl\controller\LoginValidator.java (line 44)
VARIABLE org.cysecurity.cspf.jvl.controller.LoginValidator.processRequest[1].[1].[1].[1].[1].[1].password
C:\wsast\examples\JavaVulnerableLab-master\src\main\java\org\cysecurity\cspf\jvl\controller\LoginValidator.java (line 64)
VARIABLE org.cysecurity.cspf.jvl.controller.Register.processRequest[1].[1].[1].pass
C:\wsast\examples\JavaVulnerableLab-master\src\main\java\org\cysecurity\cspf\jvl\controller\Register.java (line 44)
VARIABLE org.cysecurity.cspf.jvl.controller.XPathQuery.processRequest[1].[1].[1].pass
C:\wsast\examples\JavaVulnerableLab-master\src\main\java\org\cysecurity\cspf\jvl\controller\XPathQuery.java (line 36)
VARIABLE org.cysecurity.cspf.jvl.model.DBConnect.connect[1].[1].dbpass
C:\wsast\examples\JavaVulnerableLab-master\src\main\java\org\cysecurity\cspf\jvl\model\DBConnect.java (line 28)
Command>
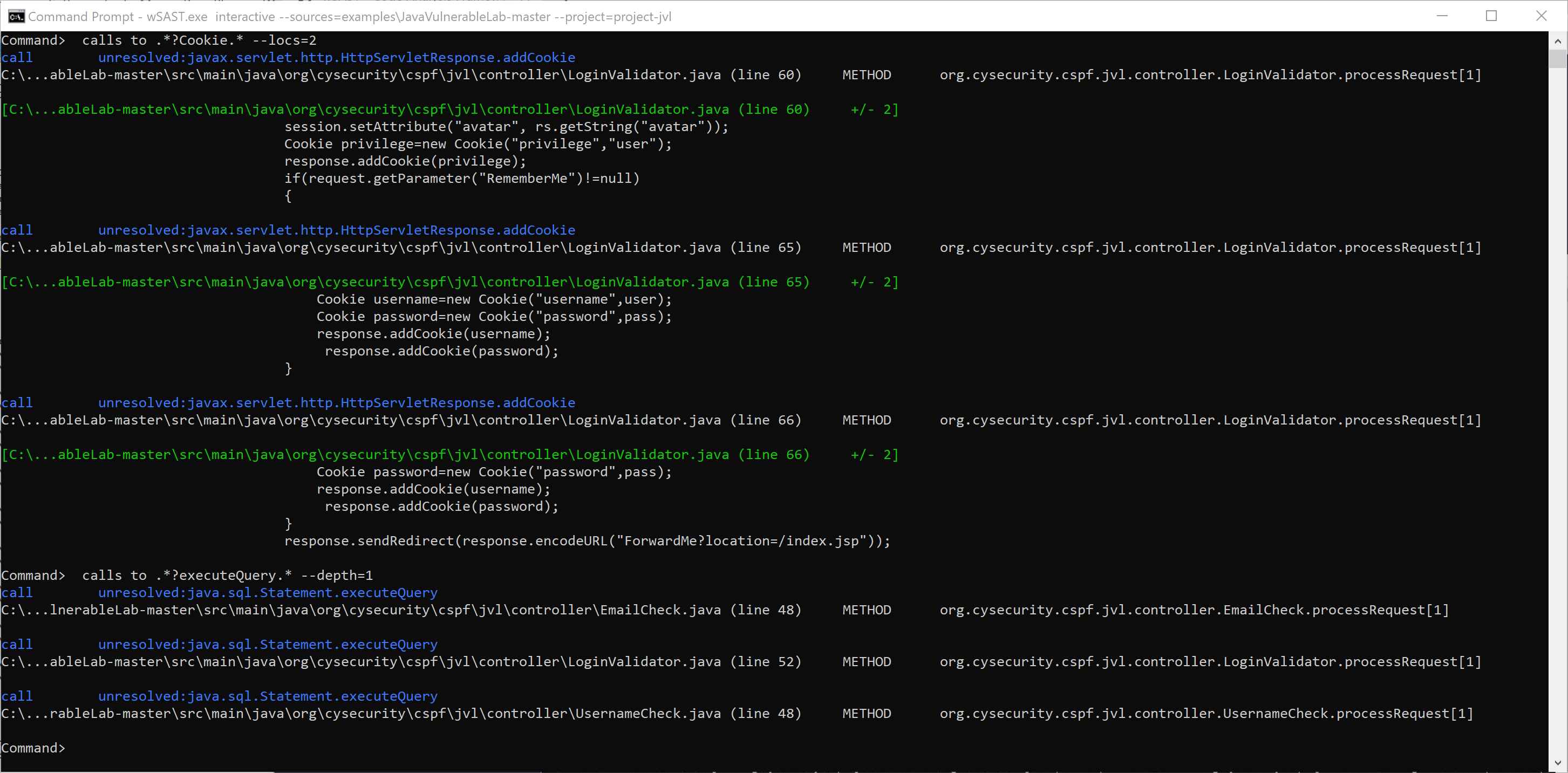
wSAST provides the ability to graph calls to and from methods matching specific names using regular expressions. The depth of the call stacks to and from the specified methods can be constrained. This can be used in an ongoing fashion when specific vulnerable functions are identified to quickly formulate potential attack paths.
Calls to specific methods:
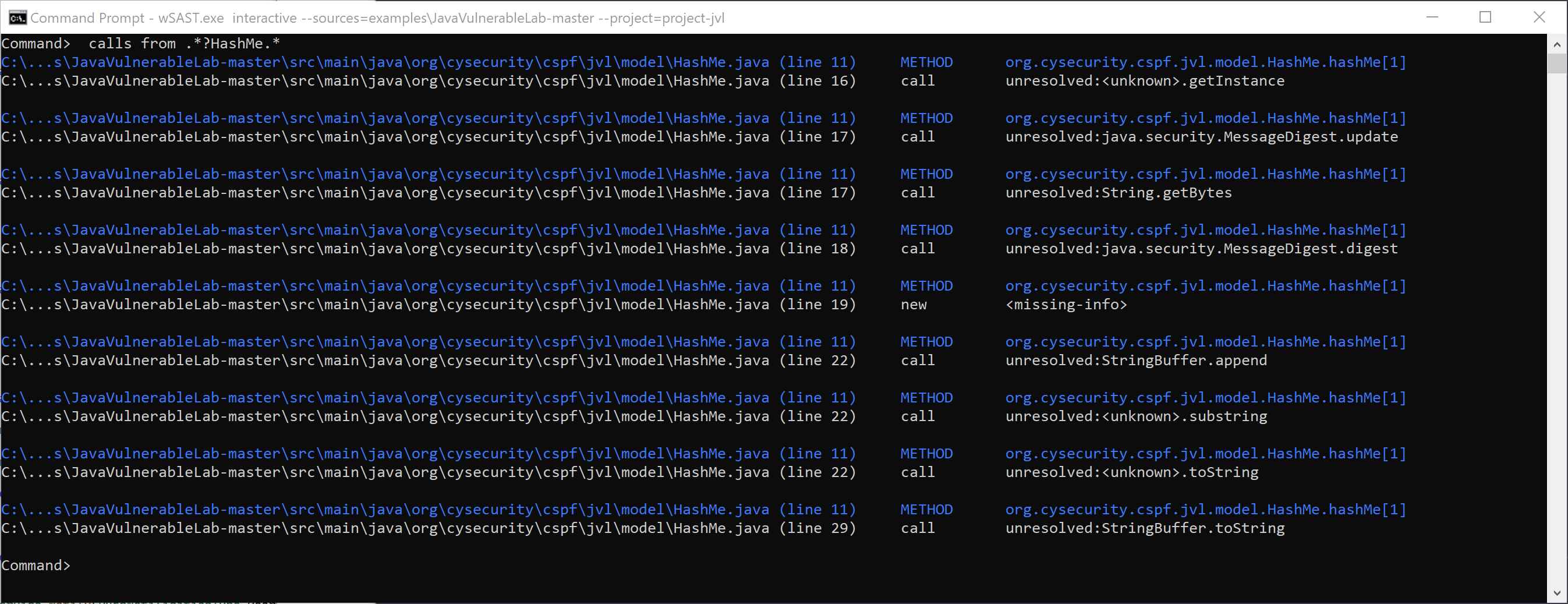
Calls from specific methods:
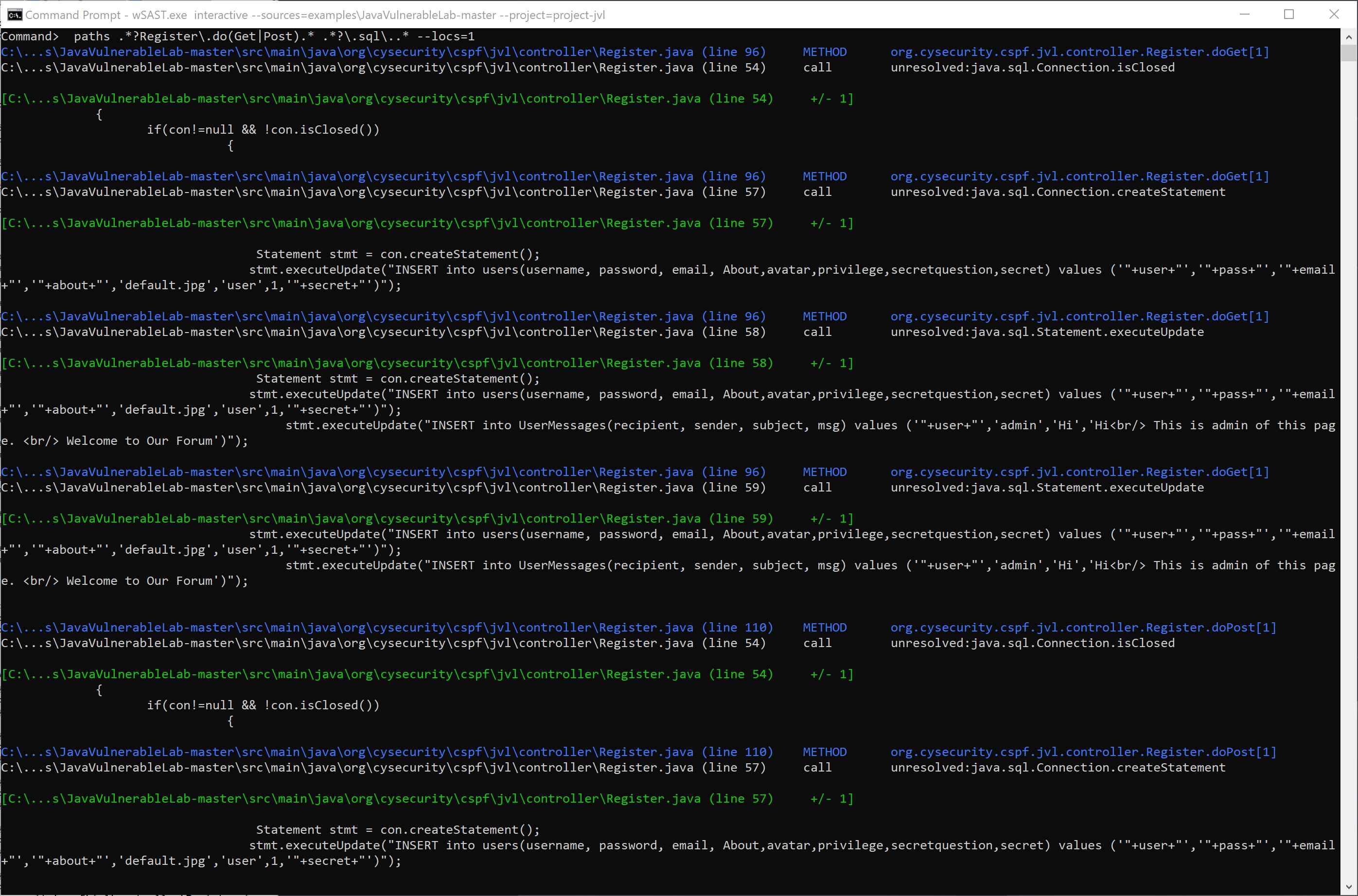
wSAST facilitates the discovery of paths between methods matching specific names and can print all matching flows. This can be used to quickly connect known classes or methods of interest, such as those involved with user inputs and database access.

Explorer the Dataflow Analyzer which forms the core capability of wSAST.
Learn more
Learn more about the Static Analysis capabilities.
Learn more
Discover the powerful code graphing capabilities which can aid you in code exploration.
Learn more
See how code searching can help you quickly determine possible paths to exploitation.
Learn more